
Renewable vitality sources, together with solar energy methods, are quickly changing into important parts of energy grids all through the world — particularly within the U.S. and Europe. Nevertheless, cybersecurity for these methods is commonly an afterthought, making a rising threat to grid safety, stability and availability.
New research from community safety answer supplier Forescout discovered an insecure ecosystem — with harmful vitality and nationwide safety implications. Whereas every residential photo voltaic system produces restricted energy, their mixed output reaches dozens of gigawatts — making their collective impression on cybersecurity and grid reliability too vital to disregard.
Within the full report, Forescout critiques identified points and presents new vulnerabilities discovered on three main solar energy system producers: Sungrow, Growatt and SMA. Forescout additionally discusses life like energy grid assault situations that may very well be executed and will trigger emergencies or blackouts, and offers advisable threat mitigation actions for house owners of sensible inverters, utilities, machine producers and regulators.
Abstract of findings
- Forescout cataloged 93 earlier vulnerabilities on solar energy and analyzed developments:
- There’s a mean of over 10 new vulnerabilities disclosed per yr prior to now three years
- 80% of these have a excessive or crucial severity
- 32% have a CVSS rating of 9.8 or 10 which usually means an attacker can take full management of an affected system
- Essentially the most affected parts are photo voltaic screens (38%) and cloud backends (25%). Comparatively few vulnerabilities (15%) have an effect on photo voltaic inverters instantly
- As a consequence of rising issues over the dominance of foreign-made solar energy parts, Forescout analyzed their frequent international locations of origin:
- 53% of photo voltaic inverter producers are based mostly in China
- 58% of storage system and 20% of the monitoring system producers are in China
- The second and third commonest international locations of origin for parts are India and the US
- New vulnerabilities:
- Forescout analyzed six of the highest 10 distributors of solar energy methods worldwide: Huawei, Sungrow, Ginlong Solis, Growatt, GoodWe, and SMA
- Forescout discovered 46 new vulnerabilities affecting completely different parts in three distributors: Sungrow, Growatt and SMA.
- These vulnerabilities allow situations that impression grid stability and person privateness
- Some vulnerabilities additionally permit attackers to hijack different sensible gadgets in customers’ houses
Influence on Grid Safety
The brand new vulnerabilities, which have now been mounted by the affected distributors, may permit attackers to take full management of a whole fleet of solar energy inverters through a few situations, as proven within the report:
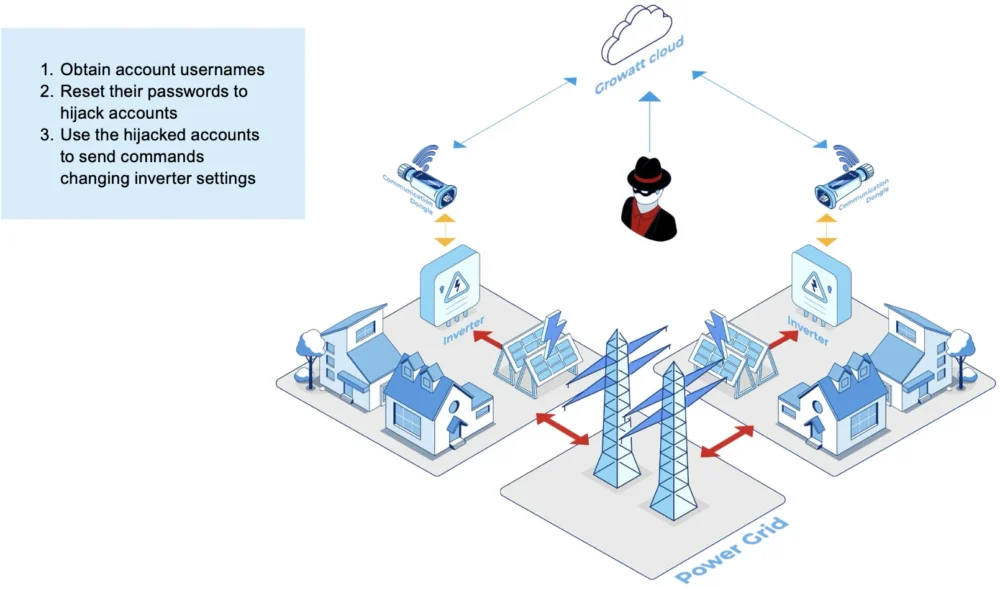 As soon as in charge of these inverters, attackers can tamper with their energy output settings or swap them on and off in a coordinated method as a botnet. The mixed impact of the hijacked inverters produces a big impact on energy era in a grid. The impression of this impact is dependent upon that grid’s emergency era capability and how briskly that may be activated.
As soon as in charge of these inverters, attackers can tamper with their energy output settings or swap them on and off in a coordinated method as a botnet. The mixed impact of the hijacked inverters produces a big impact on energy era in a grid. The impression of this impact is dependent upon that grid’s emergency era capability and how briskly that may be activated.
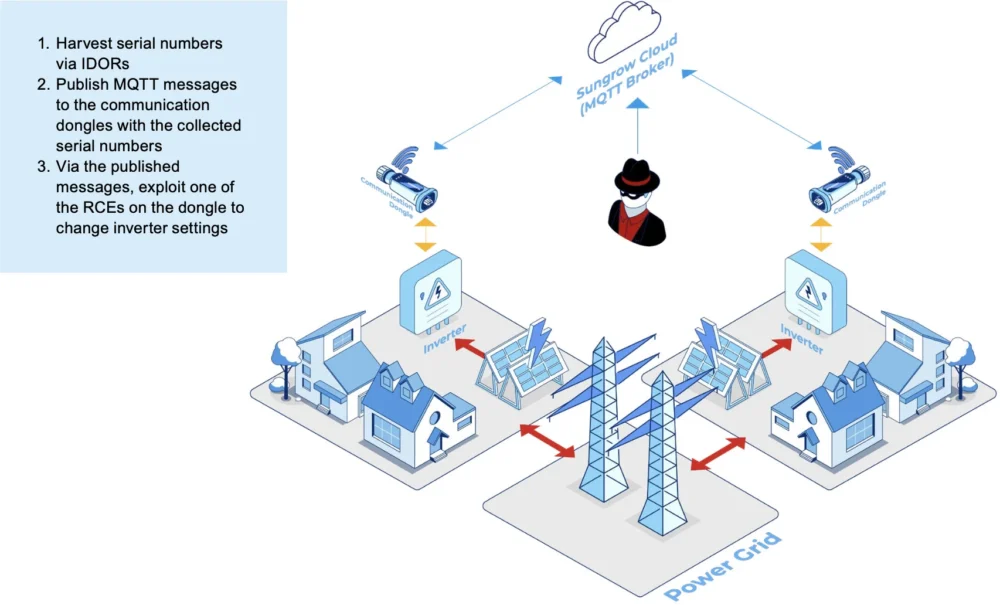
The instance Forescout discusses within the full report is that of the European grid. Earlier analysis confirmed that management over 4.5 GW can be required to convey the frequency right down to 49Hz — which mandates load shedding. Since present photo voltaic capability in Europe is round 270 GW, it will require attackers to regulate lower than 2% of inverters in a market that’s dominated by Huawei, Sungrow and SMA.
Suggestions
- Deal with PV inverters in residential, industrial, and industrial installations as crucial infrastructure:
- Homeowners of business and industrial installations ought to:
- Embody safety necessities in procurement
- Conduct a threat evaluation when establishing gadgets
- Guarantee community visibility into solar energy methods
- Section and monitor gadgets into their very own sub-networks
- Machine producers ought to:
- Implement safe software program lifecycle practices
- Conduct common penetration testing
- Undertake security-in-depth methods utilizing internet software firewalls
- Use third-party audits of communication hyperlinks based mostly on requirements, comparable to: ETSI EN 303 645, Radio Tools Directive (RED) and Cyber Resilience Act (CRA)
Information merchandise from Forescout
Trending Merchandise











